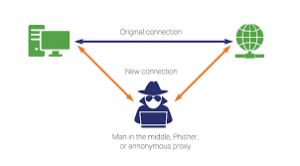
A man in the middle attack is the attack a bitch the attacker will be positioning himself or herself between the two users to overhear their conversation and interrupt the transferring of data. This is considered to be a very common type of cyber attack in which the attacker will be intercepting the communication as well as message sheeters between two parties by literally inserting themselves as the silent observer as well as a manipulator on the whole process. Every time the user will be directing the server of the website the session ID will be created and the attacker through this particular it will be secretly capturing the session ID to eavesdrop or manipulate the content to ultimately steal the data like login credentials, financial data on the other personal information with the aim of this using it for different kinds of transactions. Majorly there will be three players in this particular case which would be the victim, the person, or the application that is interacting with the victim and the attacker.
How will the MiTM attack happen?
An excellent man in the middle tackle always helps following a straightforward approach in which the attacker will be a pain in the access to a conversation and will be starting to eavesdrop in the whole process. After this, the attacker will become the main middle to intercept any kind of messages which will be shared between two bodies. The attacker will be either stealing the data or altering any kind of message to gain control over the position and perform different kinds of financial transactions. It is of two types:
- Network traffic intersection: This will be the time which has been observed as free Wi-Fi available and somebody will be connecting to it. The Wi-Fi provider can significantly steal the data in the background
- Mobile app network security: This will be coming from the well-known debate between HTTPS and HTTP. It Is Very common sense to use this particular concept because most of the applications will be based upon the right kind of systems only. Depending upon the implementation of this particular aspect is a good idea so that there is no chance of any kind of security loopholes in the whole process.
Different types of man in the middle attacks have been explained as follows:
- Email hijacking: In this particular case the attacker will be targeting the victim’s email address to gain access and communication between the target institution so that special attention will be given to the whole thing and there is no chance of any kind of problem in the whole process. In this particular case, everybody will be able to deal with the sensitive information very successfully so that there is a bare minimum chance of any kind of problematic scenario.
- Session hijacking: This will be occurring through the cross-site scripting systems or stealing session browser cookies what is ample whenever the user will be logging into the bank account the attack and will be watching was feeling the session cookie while the session will be still on. Hence, this particular aspect is very much important to be checked out in the whole process.
- Wi-Fi eavesdropping: In this particular case the attack and will be setting up the legitimate sounding Wi-Fi connection name of public Wi-Fi connection which will not require any kind of password. Users will always be lowered into connecting this particular network thinking that they will get the best possible facility of free Wi-Fi but it will lead to different types of issues in the long run.
- IP spoofing: The attacker will be altering the packet headers into the IP address over here so that there is no chance of any kind of issue and estimate e-commerce website will be dealt with very easily. In this particular case, the user will now be redirected to the fake similar-looking sites, and whenever the transaction will be initiated the fund will be transferred to some other accounts.
- DNS is moving: This particular process will be based upon infiltrating the DNS server and altering the website address to record the matching of their record. If the user is trying to gain access to the legitimate website and DNS spoofing occurs then the user will be perfectly redirected to the fake address through the alteration-based address in the whole process.
- HTTpSspoofing: In this particular case the domain will be exactly looking like the original with some of the minor changes into the non-ASCII characters which will be used in terms of luring the victims to enter the conversation between the legitimate websites.
- ARP spoofing: Address resolution protocol Will always help in translating the machine address to the local IP address and in this particular case the attacker will be linking the machine address to the legitimate user IP address through the fake PR messages and any data which has been sent by the user will be perfectly transmitted to the other attackers.
- MDNS spoofing: This particular concept will be the offshoot of DNS spoofing where the attacker will be using a local area network to respond to the legitimate requests with the fake data redirecting so that illegitimate websites will be dealt with very easily throughout the process.
CONCLUSION
Hence, it is very much important for people to be clear about the detection of my text so that there is no chance of any kind of problem and further it is very much advisable for the organization to depend upon the utilization of VPN and implementation of the end to end encryption for all times of communication throughout the process. Apart from this people also need to invest in strong authentication protocols so that there is no chance of any kind of problem and further depending upon the experts of the industry from the house of Appsealing is the best possible way of ensuring that everybody will be on the right track of dealing with things and monitoring of such attacks will be done in real-time.